VPN Encryption and How It Works
Who owns your data? The common-sense answer is obvious. However, strange as it may appear, it’s not always you. Almost any concerned third party can search, access, and even take advantage of your digital information.
Only top-grade encryption can remedy the situation. VPN Unlimited stands for safe access to the open internet. That’s why it offers an extremely secure AES-256 encryption protocol to reliably protect your data.
What is VPN Encryption?
Data encryption is a process of encoding messages or information in such a way that only authorized parties can access it. The primary purpose of encryption is to protect the confidentiality of digital data stored on a device or transferred via the internet or other networks.
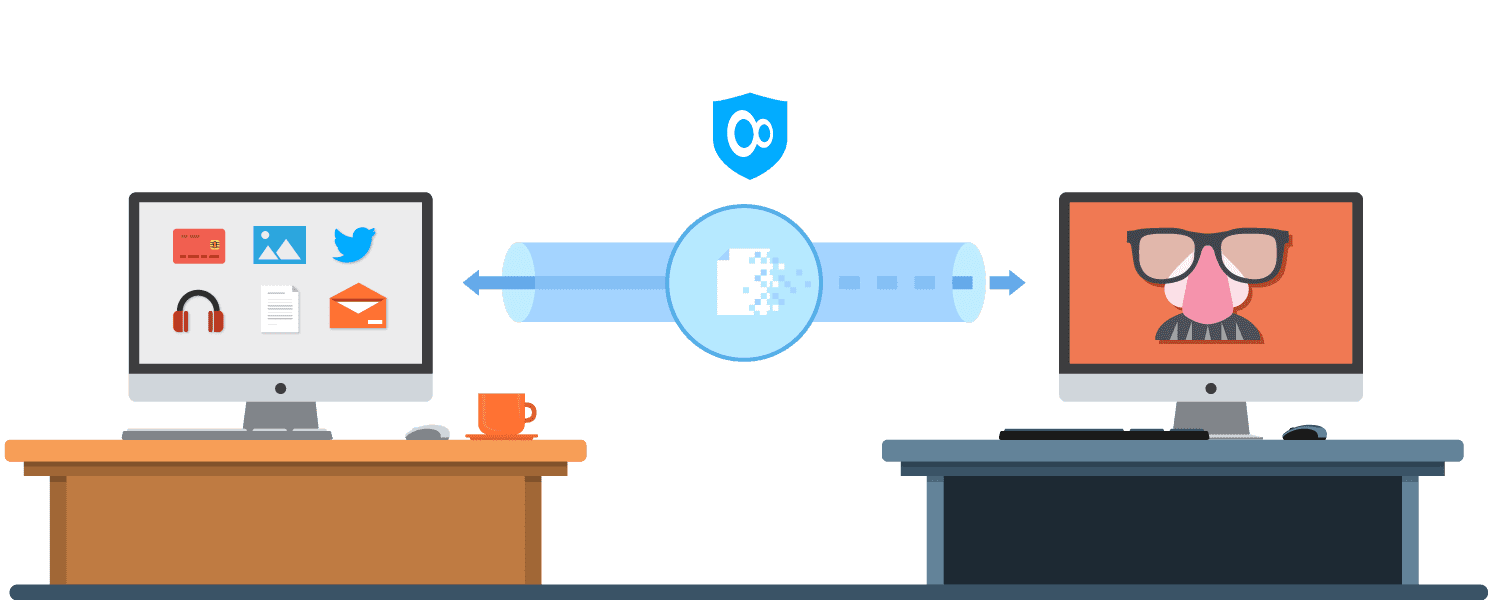
In layman terms, encryption works like a barrier between you and others in cyberspace, ensuring that no one has access to your personal data except you. It takes your internet traffic and all the information it carries and transports it through a secure, encrypted tunnel where it is scrambled and becomes gibberish. A device has to know a secret key or password that enables it to decrypt the real information to access it.
Encryption Protocols vs VPN Protocols
When discussing VPNs and encryption protocols, it’s important to distinguish them from VPN protocols.
What’s an encryption protocol
An encryption protocol, a.k.a. encryption algorithm, is a set of technologies used to encrypt your data and/or web traffic. Examples of encryption protocols include:
- AES (Advanced Encryption Standard)
- RSA (named after its inventors R. Rivest, A. Shamir, and L. Adleman)
- 3DES (Data Encryption Standard v.3)
Every encryption protocol serves different purposes and can have different subtypes. For instance, for data encryption, VPN Unlimited utilizes the 256-bit version of the AES protocol (which is more secure than its counterparts: AES-128 bit and AES-192 bit). But as you’ll see later in this piece, we use other encryption protocols for other purposes as well.
What’s a VPN protocol
A VPN protocol is a set of technologies that a VPN provider uses to deliver its services. VPN protocols vary in all sorts of technicalities, such as which encryption protocols they support or what internet ports they use. As a result, different VPN protocols provide a different speed/security ratio.
VPN Unlimited offers a variety of VPN protocols, each with its unique strengths and capabilities. You can switch protocols on the fly. It’s handy if your device doesn’t support some of the VPN protocols, or if some are blocked by your network. So choose the one with a security/speed/online freedom balance that best suits your needs.
By default, VPN Unlimited automatically uses the optimal protocol for your network, but you can easily configure your VPN app to use other protocols. Just choose the one you would like to try in your VPN settings.
Grab VPN Unlimited for the ultimate level of encryption
Do you want VPN to encrypt all traffic or just a part of it? Get any or both with VPN Unlimited!
Does VPN Encrypt All Traffic
Sometimes, it’s necessary to have a VPN encrypt all of your device’s traffic. For instance, if you’re connected to public WiFi, you don’t want any of your data to leave your device unprotected. In other cases, it’s the opposite. E.g. you may need to secure only your browser traffic without hindering the internet speed of your other apps.
VPN app to encrypt all traffic
So, let’s say you want VPN Unlimited to encrypt all the web traffic of your device. It’s vital to do so if you’re connected to the internet over a public and poorly secured WiFi, or if there’s no particular reason why you wouldn’t want to. Simply use the VPN Unlimited app and it will encrypt all the traffic of your device.
VPN extension to encrypt only browser traffic
Now, if you want to have more control over how much of your traffic our VPN encrypts, use the VPN Unlimited browser extension. In this case, VPN encryption will only affect the part of internet traffic passing through the browser. This is a great way to unblock certain sites or protect a part of your activities, while also ensuring that your other apps’ internet speed and IP address are unaffected.
How Secure is VPN Unlimited Encryption
VPN Unlimited team studiously monitors and examines possible threats to provide you with high-quality service and strong protection. That is why we offer an extremely secure, military-grade 256-bit encryption protocol.
How secure is the AES-256 encryption protocol? It’s considered to be impenetrable to brute force attacks. For instance, the U.S. Government uses AES-256 to protect top-secret, classified information. If it’s secure enough for the Government, it’s probably secure enough for most VPN Unlimited users as well.
Authentication
VPN Unlimited uses the RSA as an authentication method. It is considered one of the most secure forms of authentication. It does not rely on the network, routers, domain name servers, or a client machine. The only thing that matters is access to the private key.
The asymmetry in RSA allows a private key to be shared to encode messages without giving any information about the private key to decode messages. Therefore, this public key may be published online so that anyone can send a message to the publisher, however, only the publisher will know how to read it.
Cryptographic handshake
The cryptographic handshake is used to establish a secure connection. Its effect is highly influenced by a private key size. The longer the key is, the more secure your connection is. VPN Unlimited uses a Diffie-Hellman (DH) method with a minimum 4096-bit key and Elliptic curve Diffie-Hellman (ECDHE) protocol with 256 bits.
These encryption algorithms are extremely hard to crack, as they allow a key establishment to happen independently of the server’s private key. This gives the connection further secrecy. It’s a very useful option that protects your personal data from being decrypted even if the private key is somehow exposed.
With VPN Unlimited, your data is always well protected
No matter who you are - a traveler, a gamer, a public WiFi user, or just a citizen trying to avoid surveillance, throttling, and data theft. VPN Unlimited encryption will ensure the best protection for your data!